Key Advantages:
IMPINJ E710 supportableLong Reading ≥10mLong Reading ≥15mLong Reading ≥25m
Customization:
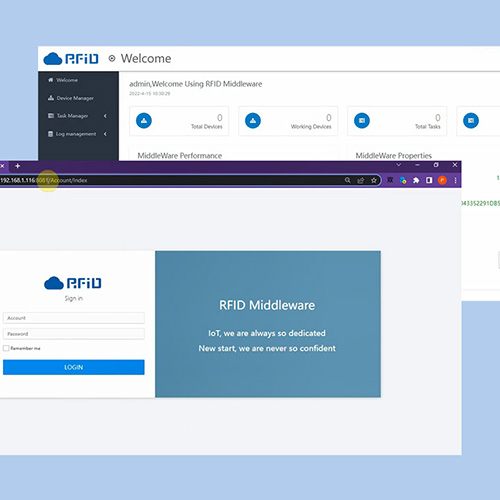
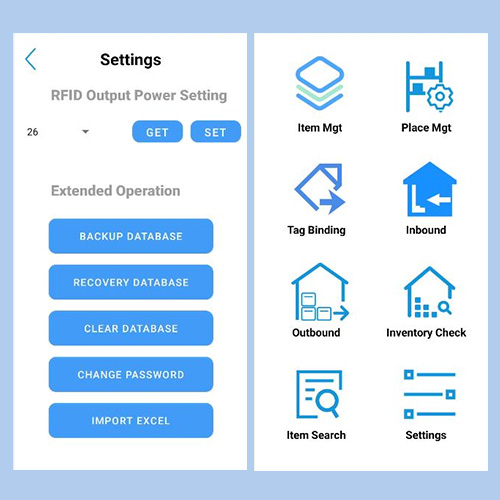
Android RFID MiddlewareInventory mini SoftwareFirmware customizedWeb management platformHttpPost Data transferRFID smart cabinet system
Applications:
Vehicle identificationAccess ControlAssest ManagementSmart ManufacturingPersonal ManagementSmart RetailSmart CitySmart Power solution
-
Vehicle Identification
-
Handheld and PDA
-
Fixed Readers
-
Integrated Reader
-
RFID System Devices
-
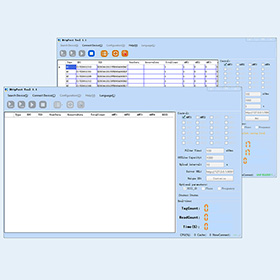
Smart Software
-
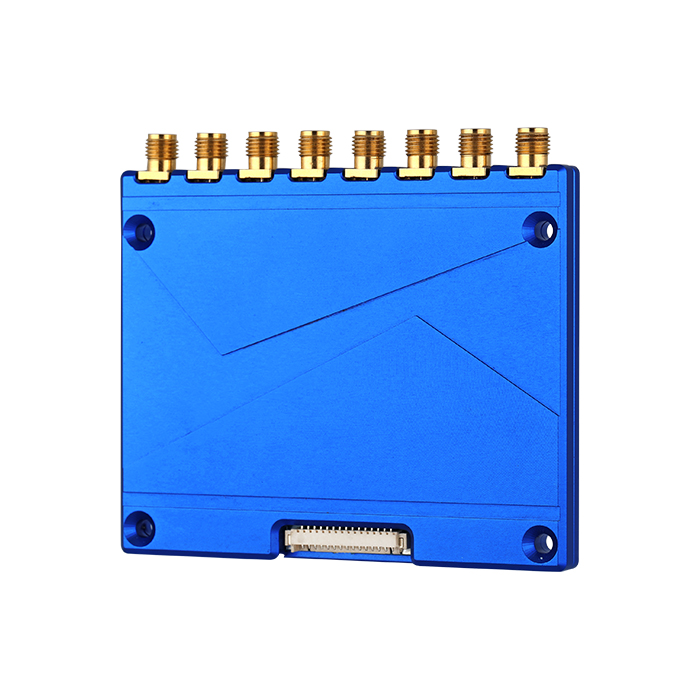
UHF Module
-
UHF Antenna
-
RFID tags
-
Industrial RFID Sensor
-
Vehicle Identification
-
Handheld and PDA
-
Fixed Readers
-
Integrated Reader
-
RFID System Devices
-
Smart Software
-
UHF Module
-
UHF Antenna
-
RFID tags
-
Industrial RFID Sensor
-
HH100
Android Integrated RFID readerNew Shine serie - Android Integrated RFID reader HH100 Smart IoT device with integrated design but support 1 additional antenna port. Running with Impinj Indy R2000 chipset/ newest Impinj E710 RAIN RFID reader chip upgradable, and operated on Otca-core Android 9.0 operation system. It not only includes built-in 4G, WiFi, and Bluetooth as standard, and PoE (IEEE 802.3 af/at/bt) optional, but also supports built-in web management functions such as remote parameter configuration, MQTT, HTTP post, MySQL database transferring and so on.View Details -
Smart HZ100
Parking System Integrated RFID ReaderHigh performance Integrated UHF RFID reader HZ100, updated from CL7206B5A, supporting ISO18000-6C protocol, long range RFID reading, fast identification, excellent multi-tag reading, strong Anti-collision, automatic reading, white list functions. Widely used fixed asset management, logistic, warehouse inventory, products tracking transshipment , e parking system vehicle management, production automation etc.View Details -
HF100
New 2-port Integrated RFID readerNew Sharp series Linux Super long reading Integrated RFID reader - HF100 2-port version integrated RFID reader is one of series Hopeland Fixed RFID Reader, integrated design but support 1 additional antenna port. Running with Impinj Indy R2000 chipset/ newest Impinj E710 RAIN RFID reader chip upgradable, and operated on Linux 2.6 operation system. It not only includes built-in 4G, WiFi, and Bluetooth, and PoE (IEEE 802.3 af/at/bt) optional, but also supports built-in web management functions such as remote parameter configuration, MQTT, HTTP post, MySQL database transferring and so on.View Details -
Sharp HF100
IP66 Parking Integrated RFID reader with 2-portNew Sharp series Linux Super long reading Integrated RFID reader - HF100 2-port version integrated RFID reader is one of series Hopeland Fixed Reader, integrated design but support 1 additional antenna port. Running with Impinj Indy R2000 chipset/ newest Impinj E710 RAIN RFID reader chip upgradable, and operated on Linux 2.6 operation system. It not only includes built-in 4G, WiFi, and Bluetooth, and PoE (IEEE 802.3 af/at/bt) optional, but also supports built-in web management functions such as remote parameter configuration, MQTT, HTTP post, MySQL database transferring and so on.View Details -
HZ100
Long reading Integrated RFID ReaderHigh performance Integrated UHF RFID reader HZ100, updated from CL7206B5A, supporting ISO18000-6C protocol, long range RFID reading, fast identification, excellent multi-tag reading, strong anti-collision, automatic reading, white list functions. Widely used fixed asset management, logistic, warehouse inventory, products tracking transshipment , e parking system vehicle management, production automation etc.View Details -
Shine HH340
ETC Free Flow RFID 4-Port Reader within Open AndroUsing Impinj R2000/E710 chip, based on the open development environment of the Android operating system. Supports MQTT to provide real-time and reliable messaging services for connecting to cloud servers, supports HTTP POST communication, and can directly send tag data to web URLs.View Details -
HH340
IoT Fixed Android RFID ReaderHopeland HH340 is a 4-port Android-based fixed RFID reader integrated with Impinj R2000/E710 RFID chip. This long range UHF RFID reader supports RJ45, RS485, Wiegand, USB, Bluetooth, WIFI, 4G, etc. as well as supports MQTT to provide real-time and reliable messaging services. It also supports sending data directly to the database.View Details -
Wing HY820
Industrial RFID Portable Data Terminal for vehicleImpinj R2000/E710 Supportable,UHF 25M Read Range;Industrial IP65 Rugged,1.5M Drop Test,Suitable For Different Harsh EnvironmentView Details -
HZ140
Mini Integrated RFID ReaderPowered by Impinj RAIN RFID E510 chip for excellent multi-tag detection performance;rich communication/software interfaces better match different application systems. Compactly Integrated design supports better deploy / installation / engineering / wiring. Customized interfaces of special application projects are expandable. It can be widely used in working station, date issuing, retail casher, check points, access control, etc.View Details -
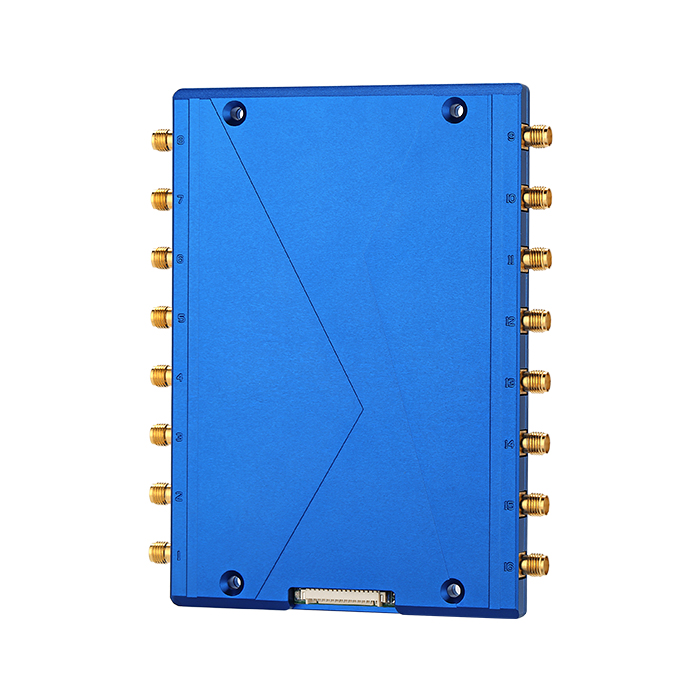
HZ380
Cost-effective 8 Ports ReaderCost-effective multi-port fixed UHF RFID reading and writing device, supports ISO18000-6C/6B two protocols, output power 0 ~ 30dBm optional, with high recognition sensitivity, fast speed, strong anti-interference ability , Multi-antenna identification efficiency.View Details -
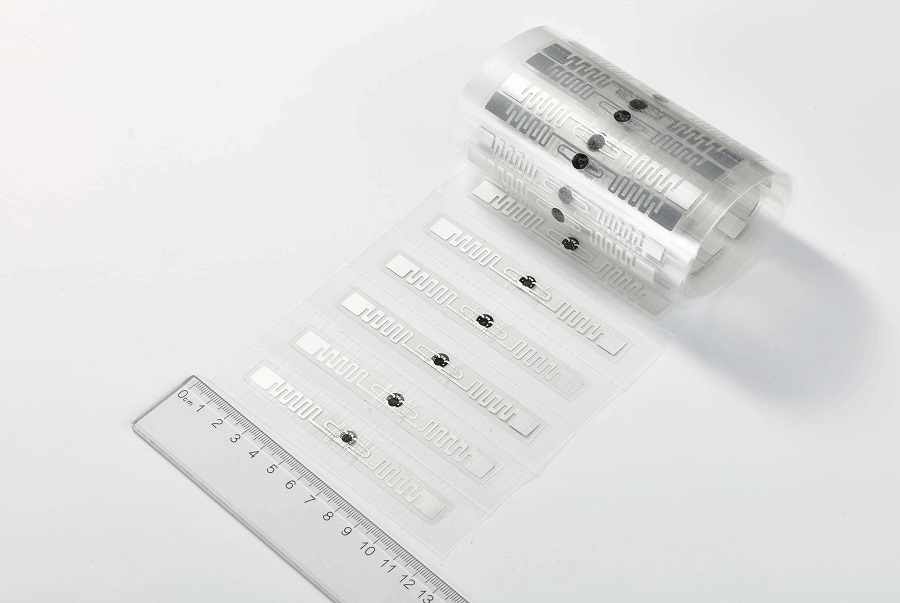
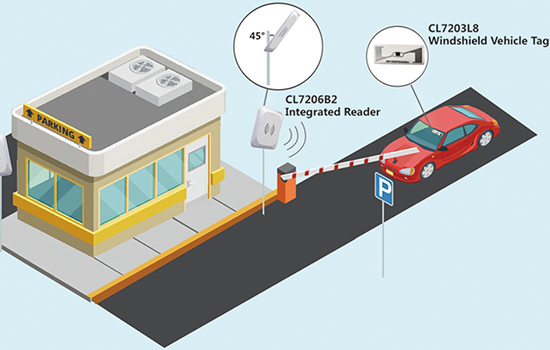
CL7203L8
RFID Windshield Tag for Vehicle managementRFID sticker/label fragile, especially designed for vehicle windshield, applications: ITS( Intelligent Transportation System), ETC(Electronic Toll Collection), vehicle management, parking management.View Details -
HF380
8 Ports Fixed ReaderIMPINJ RAIN RFID E710 high-performance RFID chip; built-in Linux, easy to customize application development; can support POE power supply at maximum power; expandable Bluetooth, WiFi wireless transmission function; support RJ-45/RS-232/RS-485 /USB/Wiegand multiple communication interfaces; support remote configuration via Web.View Details -
A0910
Outdoor use 9dBi Linear UHF Antenna for vehicle maHigh protection level, can be easily applied to various indoor and outdoor occasions in the UHF frequency band.View Details -
CL7203L8L
PET RFID Headlight Tag for Vehicle ManagementRFID sticker/label fragile, especially designed for vehicle windshield, applications: ITS( Intelligent Transportation System), ETC(Electronic Toll Collection), vehicle management, parking management.View Details -
HT100
Industrial Integrated RFID ReaderHT100 is a product independently developed by Shenzhen Hopeland Technology Co., Ltd. This product is a high-performance UHF RFID reading and writing equipment with exquisite and beautiful appearance. It supports ISO18000-6C EPC C1G2 protocol, and is mainly used in production line station management and other scenarios.View Details