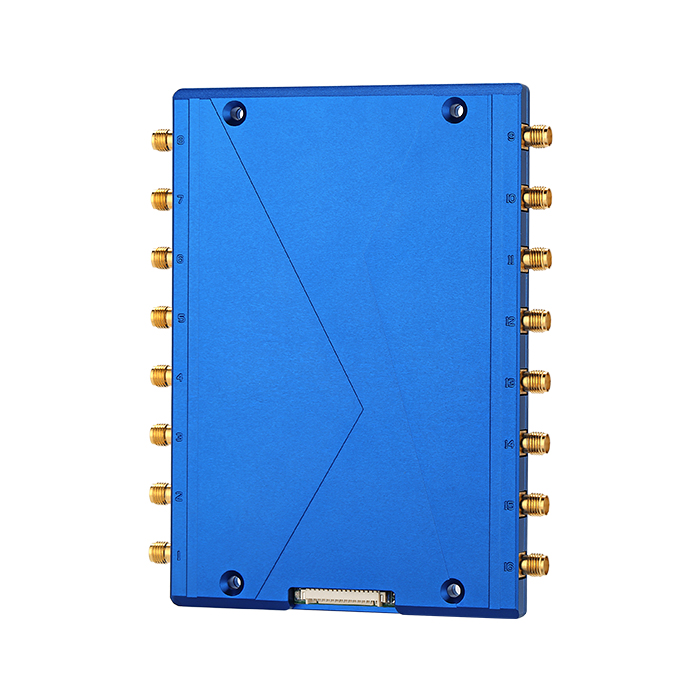
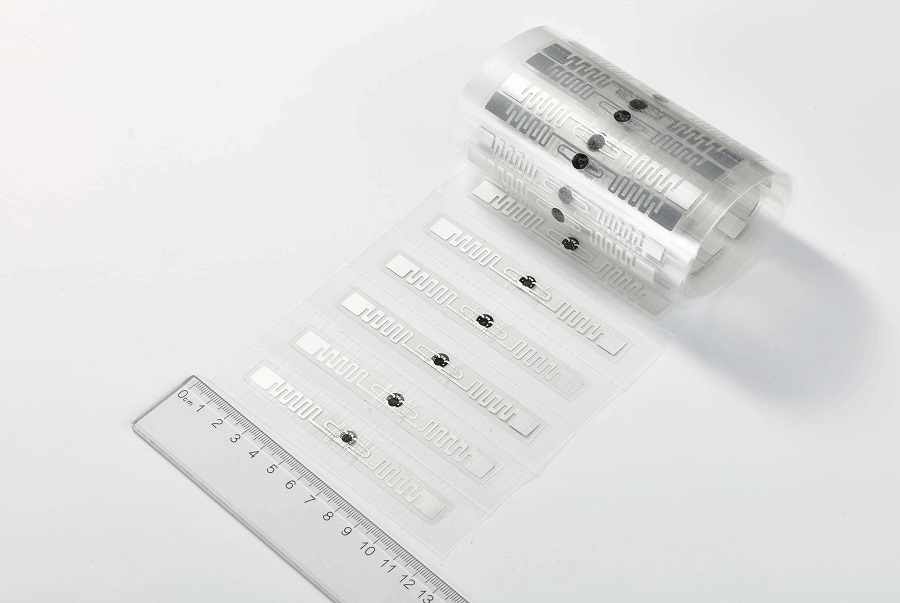
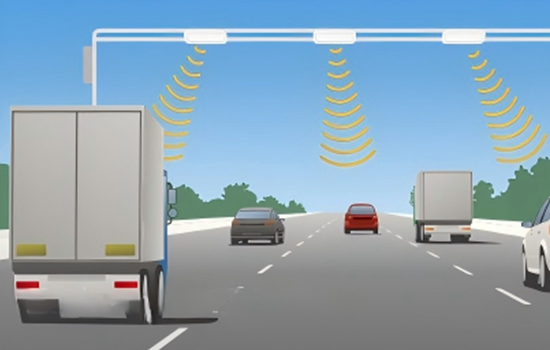
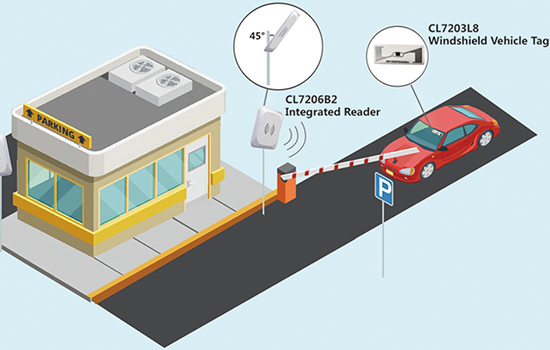
Key Advantages:
IMPINJ E710 supportableLong Reading ≥10mLong Reading ≥15mLong Reading ≥25m
Customization:
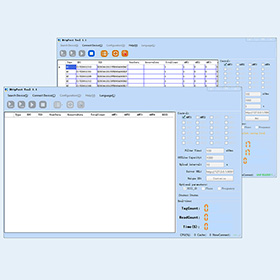
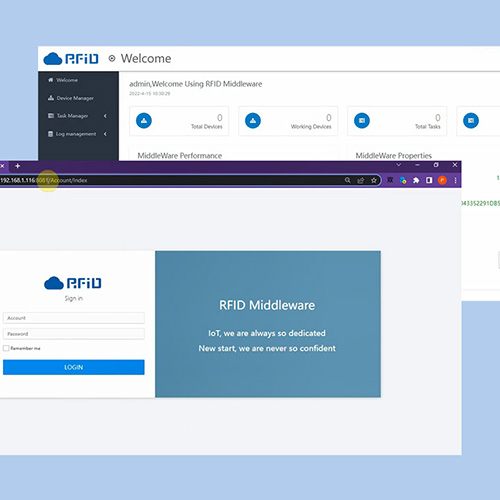
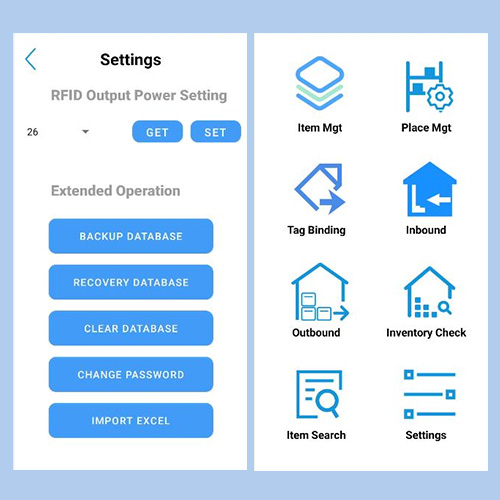
Android RFID MiddlewareInventory mini SoftwareFirmware customizedWeb management platformHttpPost Data transferRFID smart cabinet system
Applications:
Vehicle identificationAccess ControlAssest ManagementSmart ManufacturingPersonal ManagementSmart RetailSmart CitySmart Power solution
-
Vehicle Identification
-
Handheld and PDA
-
Fixed Readers
-
Integrated Reader
-
RFID System Devices
-
Smart Software
-
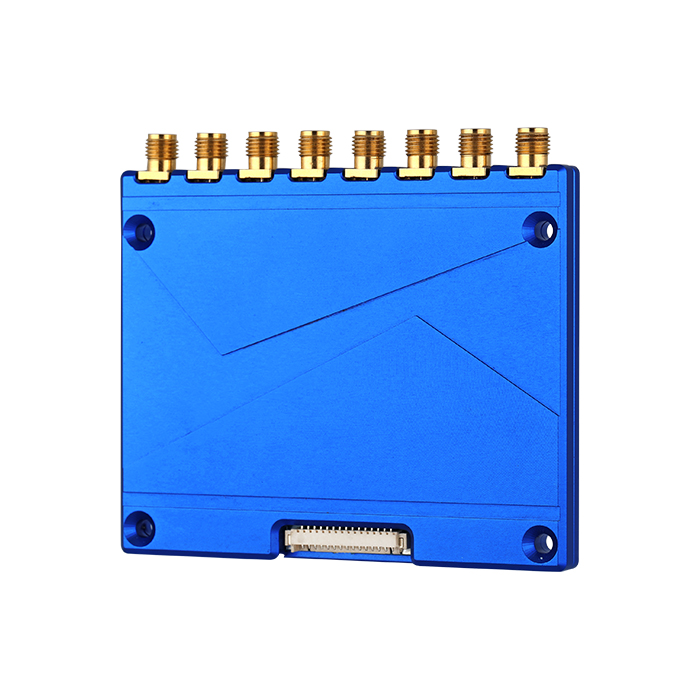
UHF Module
-
UHF Antenna
-
RFID tags
-
Industrial RFID Sensor
-
Vehicle Identification
-
Handheld and PDA
-
Fixed Readers
-
Integrated Reader
-
RFID System Devices
-
Smart Software
-
UHF Module
-
UHF Antenna
-
RFID tags
-
Industrial RFID Sensor
-
CL7203L8
RFID Tag Sticker for Vehicle WindshieldRFID sticker/label fragile, especially designed for vehicle windshield, applications: ITS( Intelligent Transportation System), ETC(Electronic Toll Collection), vehicle management, parking management.View Details -
CL7203L1
Global Class1 Gen2 Standard RFID Card CL7203L1Standard UHF RFID white card CL7203L1: Access control system, VIP card, e- Ticketing, assets management, parking system,library management, working station managemnet, etc..View Details -
HH100
Android Integrated RFID readerNew Shine serie - Android Integrated RFID reader HH100 Smart IoT device with integrated design but support 1 additional antenna port. Running with Impinj Indy R2000 chipset/ newest Impinj E710 RAIN RFID reader chip upgradable, and operated on Otca-core Android 9.0 operation system. It not only includes built-in 4G, WiFi, and Bluetooth as standard, and PoE (IEEE 802.3 af/at/bt) optional, but also supports built-in web management functions such as remote parameter configuration, MQTT, HTTP post, MySQL database transferring and so on.View Details -
CL7203H-LB
UHF Library TagHopeland UHF Library Tag CL7203H-LB powered on Impinj Chipset,supports ISO18000-6C And EPCglobal C1 Gen2 Protocol,supports Multiple Reading. The shape is slender and thin, and it can be easily hidden and installed. It is very suitable for applications in the fields of books, archives and electronic ticket management.View Details -
CL7203E-3613
RFID UHF PCB On-metal TagAlien Higgs 3 chip UHF RFID anti-metal tags, leveraging the properties of PCB substrates and special process design, offer remarkable advantages in anti-interference and environmental adaptability, perfectly meeting the item management needs for objects with metal surfaces across multiple fields such as industry and power.View Details -
Smart HZ100
Parking System Integrated RFID ReaderHigh performance Integrated UHF RFID reader HZ100, updated from CL7206B5A, supporting ISO18000-6C protocol, long range RFID reading, fast identification, excellent multi-tag reading, strong Anti-collision, automatic reading, white list functions. Widely used fixed asset management, logistic, warehouse inventory, products tracking transshipment , e parking system vehicle management, production automation etc.View Details -
S120
USB RFID Desktop Reader/WriterS120 is a convenient desktop RFID reader&writer, portable with small size, fit for production line and work station management, access control, library management. It's widely used for tag's reading, writing, authorizing and format operation.View Details -
HY830
Android 13 RFID handheld terminal2025 New Android 13.0 RFID Reader HY830 Impinj E710 chip with UHF more than 20m reading distance, powered on MTK MT6765 Octa-core 2.0GHz; Industrial IP67 rugged, 1.2M Drop to concrete, applying to kinds of severe environment.View Details -
HY820
UHF RFID handheld terminalImpinj E710 Supportable,UHF 25M Read Range;Industrial IP65 Rugged,1.5M Drop Test,Suitable For Different Harsh EnvironmentView Details -
S100
UHF cost-efficient Integrated ReaderS100 is a cost-efficient classic UHF RFID Reader based on Chinese QM100 chip, supporting ISO18000-6C protocol, middle rang RFID reading, fast identification. Widely used for vehicle management, production automation, parking system and so on.View Details -
HF100
New 2-port Integrated RFID readerNew Sharp series Linux Super long reading Integrated RFID reader - HF100 2-port version integrated RFID reader is one of series Hopeland Fixed RFID Reader, integrated design but support 1 additional antenna port. Running with Impinj Indy R2000 chipset/ newest Impinj E710 RAIN RFID reader chip upgradable, and operated on Linux 2.6 operation system. It not only includes built-in 4G, WiFi, and Bluetooth, and PoE (IEEE 802.3 af/at/bt) optional, but also supports built-in web management functions such as remote parameter configuration, MQTT, HTTP post, MySQL database transferring and so on.View Details -
CL7203H-Tie
RFID UHF Tie TagRFID UHF Tie Tag with Long Reading Distance,Waterproof and Easy CarryingView Details -
CL7203E-5213
UHF RFID PCB Anti-Metal Tag CL7203E-5213Anti-metal RFID sticker/label, suitable for metal surface, long reading distance & multiple reading: assets management, documents management,equipment management and so on.View Details -
CL7203L8L
RFID Tag Sticker for Vehicle LightRFID sticker/label fragile, especially designed for vehicle windshield, applications: ITS( Intelligent Transportation System), ETC(Electronic Toll Collection), vehicle management, parking management.View Details -
CL7203L2
UHF Paper LabelUHF Paper Label 73*34mm, Inlay 9662. Support ISO18000-6C And EPCglobal C1 Gen2 Protocol. Support Multiple Reading. Good performance up to 15-20 meters. Common for warehouse management/asset tracking application.View Details